Define Your Load Balancer
First, provide some basic configuration information for your load balancer, such as a name, a network, and a listener.
A listener is a process that checks for connection requests. It is configured with a protocol and a port for the frontend (client to load balancer) connections, and protocol and a port for the backend (load balancer to backend instance) connections. In this example, you configure a listener that accepts HTTP requests on port 80 and sends them to the containers in your tasks on port 80 using HTTP.
To define your load balancer
- Open the Amazon EC2 console at https://console.aws.amazon.com/ec2/.
- From the navigation bar, select a Region for your load balancer. Be sure to select the same Region that you selected for your Amazon ECS container instances.
- In the navigation pane, under LOAD BALANCING, choose Load Balancers.
- Choose Create Load Balancer.
- On the Select load balancer type page, choose Application Load Balancer and then chooseContinue.
- Complete the Configure Load Balancer page as follows:
- For Name, type a name for your load balancer.
- For Scheme, an internet-facing load balancer routes requests from clients over the internet to targets. An internal load balancer routes requests to targets using private IP addresses.
- For IP address type, choose ipv4 to support IPv4 addresses only or dualstack to support both IPv4 and IPv6 addresses.
- For Listeners, the default is a listener that accepts HTTP traffic on port 80. You can keep the default listener settings, modify the protocol or port of the listener, or choose Add to add another listener.NoteIf you plan on routing traffic to more than one target group, see ListenerRules for details on how to add host or path-based rules.
- For VPC, select the same VPC that you used for the container instances on which you intend to run your service.
- For Availability Zones, select the check box for the Availability Zones to enable for your load balancer. If there is one subnet for that Availability Zone, it is selected. If there is more than one subnet for that Availability Zone, select one of the subnets. You can select only one subnet per Availability Zone. Your load balancer subnet configuration must include all Availability Zones that your container instances reside in.
- Choose Next: Configure Security Settings.
(Optional) Configure Security Settings
If you created a secure listener in the previous step, complete the Configure Security Settingspage as follows; otherwise, choose Next: Configure Security Groups.
To configure security settings
- If you have a certificate from AWS Certificate Manager, choose Choose an existing certificate from AWS Certificate Manager (ACM), and then choose the certificate from Certificate name.
- If you have already uploaded a certificate using IAM, choose Choose an existing certificate from AWS Identity and Access Management (IAM), and then choose your certificate from Certificate name.
- If you have a certificate ready to upload, choose Upload a new SSL Certificate to AWS Identity and Access Management (IAM). For Certificate name, type a name for the certificate. For Private Key, copy and paste the contents of the private key file (PEM-encoded). In Public Key Certificate, copy and paste the contents of the public key certificate file (PEM-encoded). In Certificate Chain, copy and paste the contents of the certificate chain file (PEM-encoded), unless you are using a self-signed certificate and it's not important that browsers implicitly accept the certificate.
- For Select policy, choose a predefined security policy. For details on the security policies, see Security Policies.
- Choose Next: Configure Security Groups.
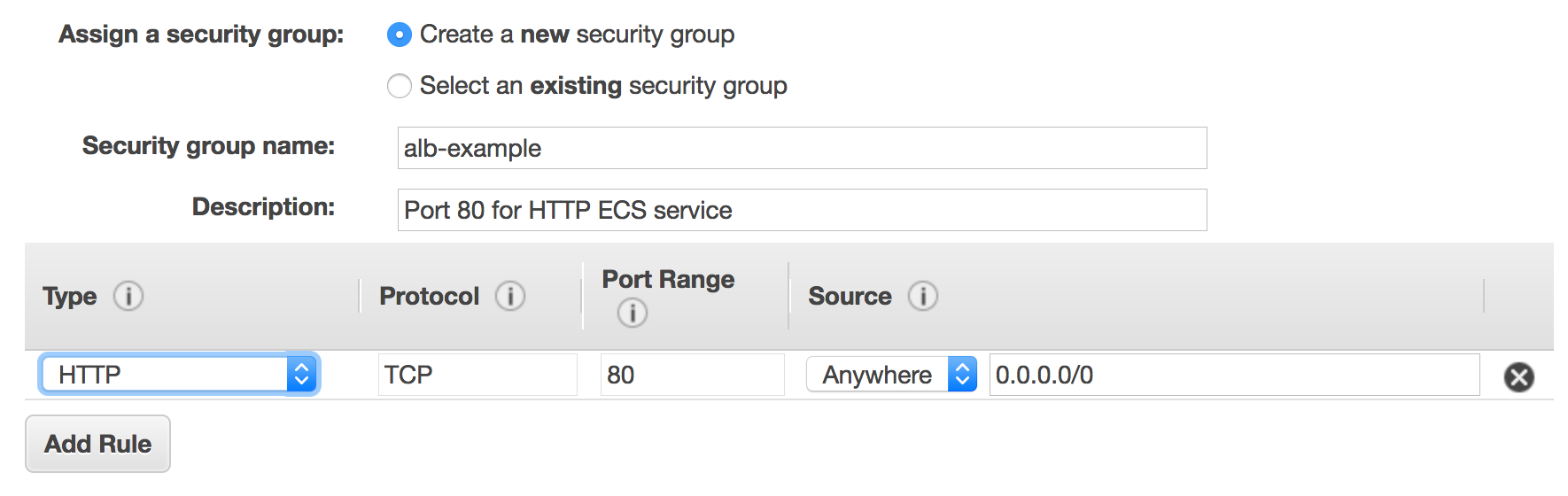
Configure Security Groups
You must assign a security group to your load balancer that allows inbound traffic to the ports that you specified for your listeners. Amazon ECS does not automatically update the security groups associated with Elastic Load Balancing load balancers or Amazon ECS container instances.
To assign a security group to your load balancer
- On the Assign Security Groups page, choose Create a new security group.
- Enter a name and description for your security group, or leave the default name and description. This new security group contains a rule that allows traffic to the port that you configured your listener to use.NoteLater in this topic, you create a security group rule for your container instances that allows traffic on all ports coming from the security group created here, so that the Application Load Balancer can route traffic to dynamically assigned host ports on your container instances.
- Choose Next: Configure Routing to go to the next page in the wizard.
Configure Routing
In this section, you create a target group for your load balancer and the health check criteria for targets that are registered within that group.
To create a target group and configure health checks
- For Target group, keep the default, New target group.
- For Name, type a name for the new target group.
- Set Protocol and Port as needed.
- For Target type, choose whether to register your targets with an instance ID or an IP address.ImportantIf your service's task definition uses the
awsvpcnetwork mode (which is required for the Fargate launch type), you must chooseipas the target type, notinstance. This is because tasks that use theawsvpcnetwork mode are associated with an elastic network interface, not an Amazon EC2 instance. - For Health checks, keep the default health check settings.
- Choose Next: Register Targets.
Register Targets
Your load balancer distributes traffic between the targets that are registered to its target groups. When you associate a target group to an Amazon ECS service, Amazon ECS automatically registers and deregisters containers with your target group. Because Amazon ECS handles target registration, you do not add targets to your target group at this time.
To skip target registration
- In the Registered instances section, ensure that no instances are selected for registration.
- Choose Next: Review to go to the next page in the wizard.
Review and Create
Review your load balancer and target group configuration and choose Create to create your load balancer.
Create a Security Group Rule for Your Container Instances
After your Application Load Balancer has been created, you must add an inbound rule to your container instance security group that allows traffic from your load balancer to reach the containers.
To allow inbound traffic from your load balancer to your container instances
- Open the Amazon EC2 console at https://console.aws.amazon.com/ec2/.
- In the left navigation, choose Security Groups.
- Choose the security group that your container instances use. If you created your container instances by using the Amazon ECS first run wizard, this security group may have the description, ECS Allowed Ports.
- Choose the Inbound tab, and then choose Edit.
- For Type, choose All traffic.
- For Source, choose Custom, and then type the name of your Application Load Balancer security group that you created in Configure Security Groups. This rule allows all traffic from your Application Load Balancer to reach the containers in your tasks that are registered with your load balancer.
- Choose Save to finish.
Create an Amazon ECS Service
After your load balancer and target group are created, you can specify the target group in a service definition when you create a service. When each task for your service is started, the container and port combination specified in the service definition is registered with your target group and traffic is routed from the load balancer to that container.

No comments:
Post a Comment