It adds a security layer to EC2 instances that control both inbound and outbound traffic at the instance level.
What is NACL?
NACL also adds an additional layer of security associated with subnets that control both inbound and outbound traffic at the subnet level.
Combining Security Group and NACL
Maximum number of rules that exist per NACL: 20
Maximum number of rules that can exist per Security Group: 50
Maximum number of Security Groups that can exist per instance: 5
Maximum number of rules that can exist per instance: 5*50 + 20 = 270
Differences b/w Security Group and NACL
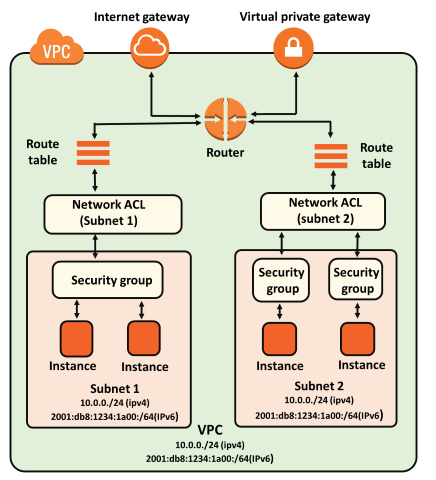
| Security Group | NACL (Network Access Control List) |
|---|---|
| It supports only allow rules, and by default, all the rules are denied. You cannot deny the rule for establishing a connection. | It supports both allow and deny rules, and by default, all the rules are denied. You need to add the rule which you can either allow or deny it. |
| It is a stateful means that any changes made in the inbound rule will be automatically reflected in the outbound rule. For example, If you are allowing an incoming port 80, then you also have to add the outbound rule explicitly. | It is a stateless means that any changes made in the inbound rule will not reflect the outbound rule, i.e., you need to add the outbound rule separately. For example, if you add an inbound rule port number 80, then you also have to explicitly add the outbound rule. |
| It is associated with an EC2 instance. | It is associated with a subnet. |
| All the rules are evaluated before deciding whether to allow the traffic. | Rules are evaluated in order, starting from the lowest number. |
| Security Group is applied to an instance only when you specify a security group while launching an instance. | NACL has applied automatically to all the instances which are associated with an instance. |
| It is the first layer of defense. | It is the second layer of defense. |
No comments:
Post a Comment