In computer and computer networks, an attacker is the individual or organization who performs the malicious activities to destroy, expose, alter, disable, steal or gain unauthorized access to or make unauthorized use of an asset.
As the Internet access becomes more pervasive across the world, and each of us spends more time on the web, there is also an attacker grows as well. Attackers use every tools and techniques they would try and attack us to get unauthorized access.
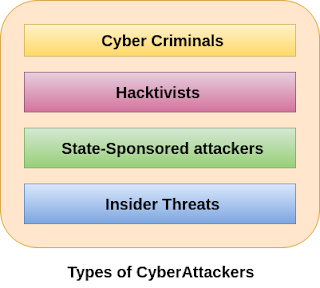
There are four types of attackers which are described below-
Cyber Criminals
Cybercriminals are individual or group of people who use technology to commit cybercrime with the intention of stealing sensitive company information or personal data and generating profits. In today's, they are the most prominent and most active type of attacker.
Cybercriminals use computers in three broad ways to do cybercrimes-
- Select computer as their target- In this, they attack other people's computers to do cybercrime, such as spreading viruses, data theft, identity theft, etc.
- Uses the computer as their weapon- In this, they use the computer to do conventional crime such as spam, fraud, illegal gambling, etc.
- Uses the computer as their accessory- In this, they use the computer to steal data illegally.
Hacktivists
Hacktivists are individuals or groups of hackers who carry out malicious activity to promote a political agenda, religious belief, or social ideology. According to Dan Lohrmann, chief security officer for Security Mentor, a national security training firm that works with states said "Hacktivism is a digital disobedience. It's hacking for a cause." Hacktivists are not like cybercriminals who hack computer networks to steal data for the cash. They are individuals or groups of hackers who work together and see themselves as fighting injustice.
State-sponsored Attacker
State-sponsored attackers have particular objectives aligned with either the political, commercial or military interests of their country of origin. These type of attackers are not in a hurry. The government organizations have highly skilled hackers and specialize in detecting vulnerabilities and exploiting these before the holes are patched. It is very challenging to defeat these attackers due to the vast resources at their disposal.
Insider Threats
The insider threat is a threat to an organization's security or data that comes from within. These type of threats are usually occurred from employees or former employees, but may also arise from third parties, including contractors, temporary workers, employees or customers.
Insider threats can be categorized below-
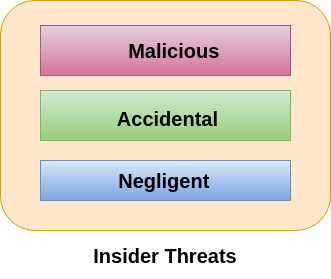
Malicious-
Malicious threats are attempts by an insider to access and potentially harm an organization's data, systems or IT infrastructure. These insider threats are often attributed to dissatisfied employees or ex-employees who believe that the organization was doing something wrong with them in some way, and they feel justified in seeking revenge.
Insiders may also become threats when they are disguised by malicious outsiders, either through financial incentives or extortion.
Accidental-
Accidental threats are threats which are accidently done by insider employees. In this type of threats, an employee might accidentally delete an important file or inadvertently share confidential data with a business partner going beyond company?s policy or legal requirements.
Negligent-
These are the threats in which employees try to avoid the policies of an organization put in place to protect endpoints and valuable data. For example, if the organization have strict policies for external file sharing, employees might try to share work on public cloud applications so that they can work at home. There is nothing wrong with these acts, but they can open up to dangerous threats nonetheless.
No comments:
Post a Comment